Cloud Security Tips

As I wrote in the first post from this sequence, this post will covered good cloud security tips for Identity and Access Management. Identity provides the basis for wide variety for security assurance, while access management protects data and resources helping you to decide who has access or not.
So, regarding these posts are merging Microsoft recommendations for Cloud Adoption and my expertise with Cloud environments and security. Keeping this in mind, one approach that I like to use it is Defense in Depth. Defense in Depth is a cybersecurity strategy that uses multiple layers of security controls to provide redundancy in case a security control fails or a vulnerability is exploited.
Identity Management
Identity management is the process of authenticating and authorizing. It also involves controlling information about those principals (identities). Those principals may include services, applications, users, groups, etc. The Microsoft Identity and Access Management ecosystem help IT protects access to applications and resources across the corporate datacenter and into the cloud.
This post focuses on some of following core Azure Identity management capabilities:
- Single sign-on
- Multi-Factor Authentication
- Azure role-based access control
- Hybrid identity management
- Privileged identity management
- Identity protection
Access Control
Once the Azure Identity core or IAM system confirms your identity, it uses access control to regulate your level of access.
On Azure you can apply the access controls in some levels, that is defined as scope.
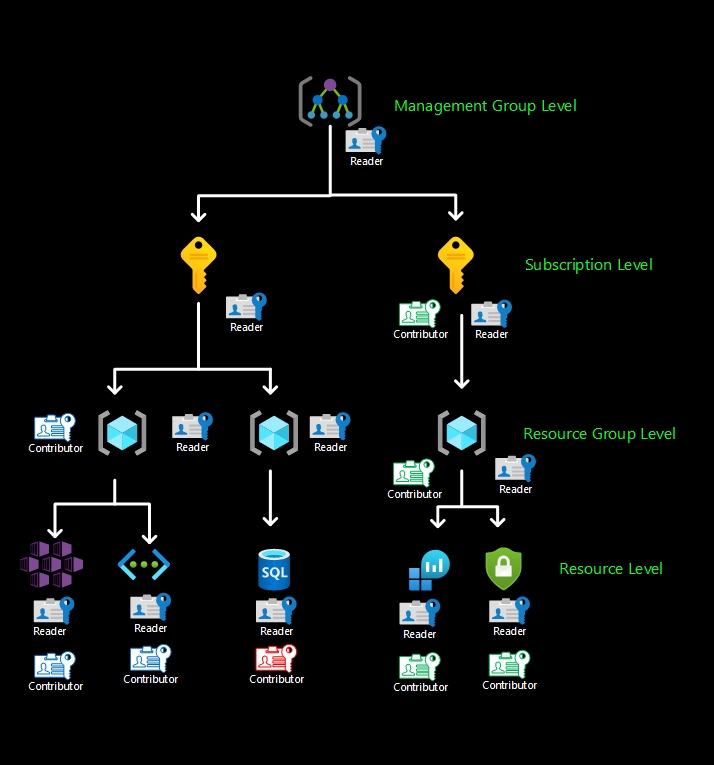
Management Group provided a governance scope above subscriptions. So once, when the permission is granted for a management group, all the resources below this management group will inherit the applied permissions.
Azure Subscription is a logical container used to provision related business or technical resource in Azure. So once, when the permission is granted for a subscription, all the resources below this subscription will inherit the applied permissions.
Resource Group is a container that holds related resources for an Azure solution. The permissions granted for a resource group, will be inherited by the resources into this resource group.
Resource is an entity managed by Azure, such as virtual machines, virtual networks, storages accounts, and etc. The permissions granted for this resources only will be applied for this one.
Deny assignments, previously, it was not supported, but now it supports deny assignment in a limited way.Similar to a role assignment, a deny assignment attaches a set of deny actions to a user, group, service principal, or managed identity at a particular scope for the purpose of denying access. A role assignment defines a set of actions that are allowed, while a deny assignment defines a set of actions that are not allowed.
Azure Active Directory
Azure Active Directory is a cloud-based identity and access management service. Azure AD enables your company access external such as Microsoft 365, Azure Portal, and thousand of third parties application at SaaS (Software-as-a-Service) mode.
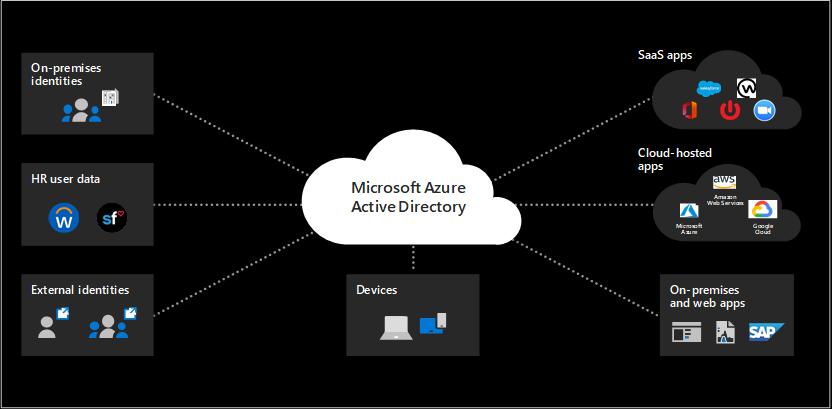
Azure AD integrations are available to works with SAP Single Sign-on(SSO), giving your company all the security features for Azure AD, such as Multi-Factor Authentication, Conditional Access, and etc.
Multi-factor authentication
Passwords are the weakest link in a security chain and a single point of failure without ant additional verification. Multi-factor authentication is a process in which a user is prompted for additional forms of identification during sign-in event.

Conditional Access
It’s critical for all the workloads that only the right people with the right resources on secure device can access company’s data from anywhere. Microsoft Conditional Access is an intelligent policy engine built for this challenge. Its robust controls allow you to define specific conditions for how user authenticate and gain access to apps and data.
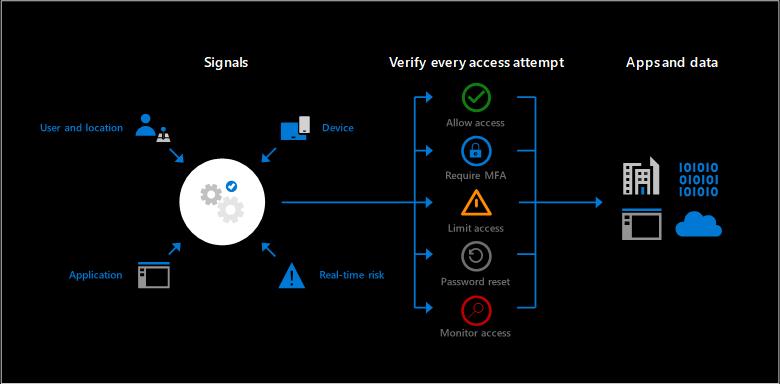
Microsoft Conditional Access gives the company the power to enforce the core of principles of Zero Trust, never trust, always verified.
For example, you might have have a policy that requires MFA if the user attempts access from a new location.
Hybrid Identity
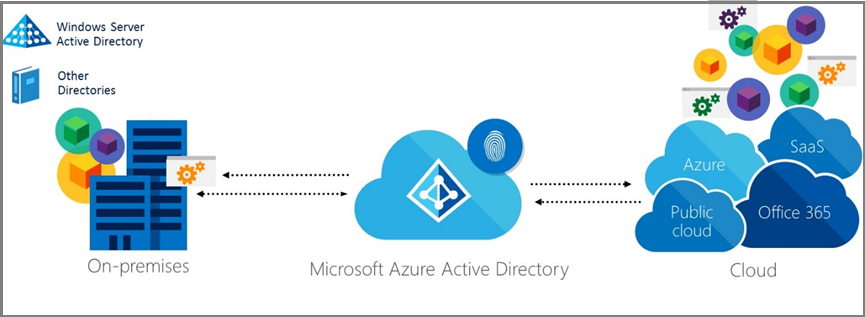
The key is decide a good design for hybrid identities, determine your needs and requirements. The first step is define what the identity requirements, if you are looking to cut IT operational cost, or secure cloud assets, or modernize your IT, and etc. Defines how directory will be synchronization, is about providing users an identity in the cloud base on their on-premises identity. If the user will have multifactor or not, and etc.
Define your strategy for enhancing data security through strong identity, determine your data protection requirements, the content management needs, access control, data protection strategy.
And the important one, planning your hybrid identity lifecycle. Identity is one of the foundations of your enterprise mobility and application access strategy. Leaving an unused identity with access is one more loophole for an attack vector.
Azure Role-based access
Access management for cloud resources is a critical function for any organization that is using or planning to move for cloud. Azure Role-Based Access Control (Azure RBAC) helps to manage who has access to Azure resources, what they can do with those resources, and what areas the have access to.
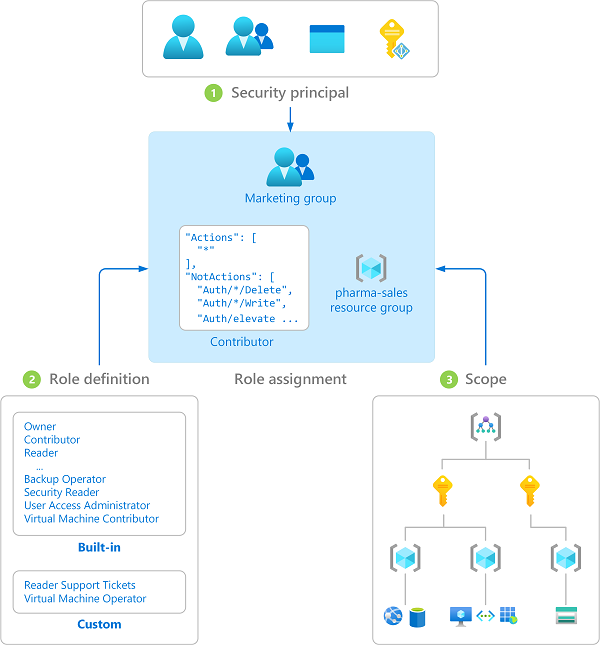
It’s an authorization system built level, that provides fine-grained access management to resources. For understand, the key it’s how to works. A role assignment consists of three elements:
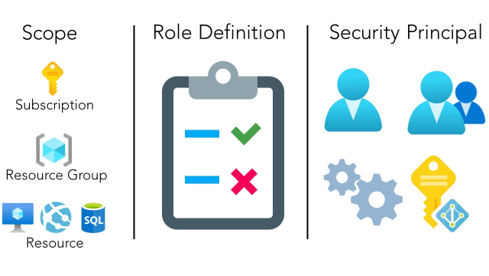
Security principal is an object that represents a user, group, service principal, or managed identity that is requesting access to Azure resources.
Role definition is collection of permissions. It’s typically just called a role. A role definition lists the actions that can be performed, such as read, write, and delete.
Role definition is collection of permissions. It’s typically just called a role. A role definition lists the actions that can be performed, such as read, write, and delete. Roles can be high-level, like owner (highest permission), or specific, like virtual machine reader or only reader. If the built-in roles don’t meet the specific needs of your requirements, you can create your own Azure custom roles.
Scope is the set of resources that the access applies to. In Azure, you can specify a scope at four levels: management group, subscriptions, resource group, or resource.
Azure Privileged Identity Management
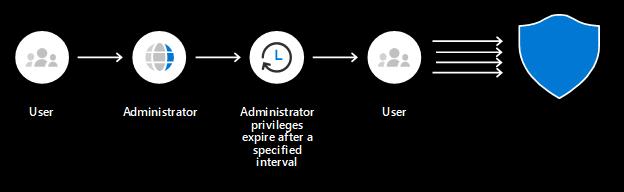
Privileged Identity Management (PIM) is a service in Azure AD that give you the manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online services, such as Microsoft 365 or Microsoft Intune.
Azure PIM provide just-in-time privileged access to Azure AD and Azure resources. Your company admin can assign time-bound access to resources using start and end dates.
You can require approval before to activate privileged roles. Use justification for tracking the privileged roles activiation.
Next Post
In the next one, following defense in depth approach I will cover the network side. Such as topology, network security segregation, and etc.
Leave a Reply