Cloud Security Tips

Your company relies on SAP systems to execute vital business operations, encompassing essentials data such as finance, payroll, and employee information.Safeguarding this data is of paramount importance, as it carries significant businnes impact. Consequently, ensuring the security of your SAP infrastructure stands as a critical components in effectively managing your SAP system landscape.
The security of the SAP environment is a complex area as I said in the begining of this sequence of posts, and you need to ensure that you have secured each components of the service layer. Azure is the most common choice for the customers migrating their workload to the cloud. Bellow is a description of the different elements comprising the Infrastructure as a Service (IaaS) layer in Azure, accompanied by the corresponding responsibilities of each party involved. In the IaaS model, you assume the role managing the operating system, middleware, runtime, data and application layers. As a result, it becomes your responsability to customize the security measures within these layers according to your company’s specific requirements.
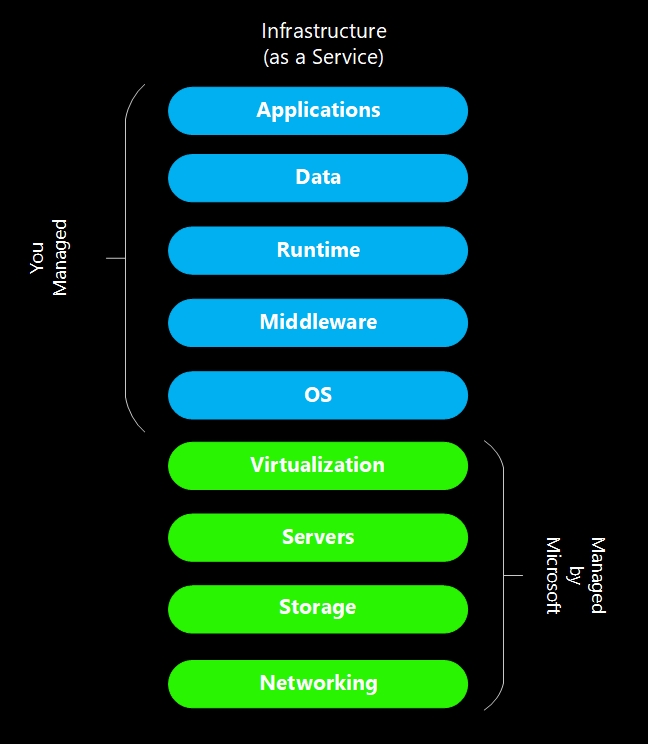
Securing the operating system is a vital aspect to ensure optimal performance of your SAP workload applications and serves as the gateway for your virtual machine. Therefore, prioritizing the security of the operating system is challenger. By default, the operating system images provided on the Azure Marketplace are not inherently secure, as they are equipped with only basic security measures. Thus, it is crucial to implement additional security measures to fortify the operating system and safeguard your SAP environment effectively.
What is hardening image?
A hardened image refers to a pre-configured operating system or software image that has undergone various security measures and configurations to enhance its resilience against potential cyber threats and attacks. The process of hardening involves implementing security best practices and mitigating vulnerabilities to create a more secure computing environment.
When an image is hardened, it is customized with security settings, patches, and configurations to minimize potential attack vectors and reduce the likelihood of successful exploitation. Some common steps involved in hardening an image include:
- Applying security patches and updates: ensuring that the image is up to date with the latest software patches and fixes, addressing known vulnerabilities.
- Removing unnecessary services and features: disisabling or removing any non-essential services, protocols, or software components that could introduce potential security risks.
- Configuring strong authentication and access controls: implementing robust authentication mechanisms, enforcing strong password policies, and setting up appropriate access controls to limit unauthorized access.
- Configuring strong authentication and access controls: implementing robust authentication mechanisms, enforcing strong password policies, and setting up appropriate access controls to limit unauthorized access.
- Enabling encryption: configuring encryption protocols to protect data at rest and in transit, such as full disk encryption or using secure communication protocols.
- Configuring firewalls and network settings: defining firewall rules and network configurations to restrict access and control network traffic.
- Logging and monitoring: enabling logging mechanisms to track and monitor system activities, helping to detect and respond to security incidents effectively.
The CIS Benchmark is a set of best practices and guidelines developed by the Center for Internet Security to enhance the security of software, operating systems, and infrastructure components. It provides specific recommendations on security configurations, controls, and system settings to reduce vulnerabilities and protect against cyber threats. Organizations can leverage CIS Benchmarks as a baseline for securing their IT infrastructure and aligning with industry-recognized security standards. Implementing these recommendations helps organizations harden their systems and strengthen their overall security posture.
Hardening Profile for Linux
The CIS Hardening Profile for Linux covers various aspects of system security, including user authentication, file system permissions, network settings, service configurations, and more. It provides specific instructions on how to secure the Linux operating system by implementing recommended security controls and configurations.
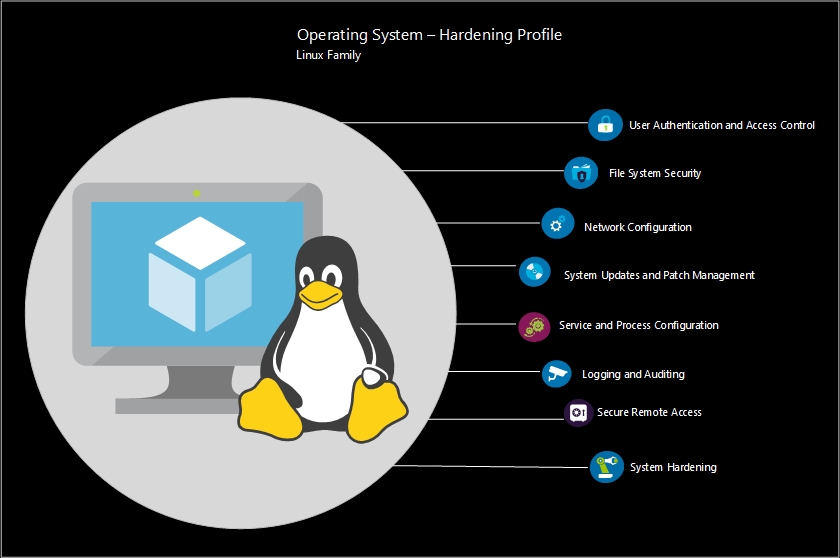
- User Authentication and Access Controls: recommendations for strong password policies, enforcing password complexity, implementing account lockout policies, and managing user privileges.
- File System Security: guidelines for setting appropriate file and directory permissions, restricting access to sensitive files, securing system files, and limiting executable permissions.
- Network Configuration: recommendations for securing network services, disabling unnecessary network protocols and services, configuring firewall rules, and implementing network segmentation.
- System Updates and Patch Management: recommendations for regularly applying security patches and updates to the Linux operating system and installed software packages.
- Service and Process Configuration: instructions for configuring and securing various services and processes running on the Linux system, such as web servers, databases, and application services.
- Logging and Auditing: enabling logging mechanisms to track and monitor system activities, helping to detect and respond to security incidents effectively.
- Secure Remote Access: guidelines for securing remote access to Linux systems, including the use of secure protocols (e.g., SSH), disabling remote root login, and implementing two-factor authentication.
- System Hardening: recommendations for disabling unnecessary system services, restricting root access, implementing secure boot settings, and securing the boot loader.
These are just some examples of the security controls covered in the CIS Hardening Profile for Linux. The profile provides detailed guidance on additional controls, configurations, and best practices to help you and your organization improve the security of their Linux-based systems.
Hardening Profile for Windows
The CIS Hardening Profile for Windows comprises a comprehensive set of security controls and recommendations to enhance the security of Windows-based operating systems. It provides guidelines for implementing security configurations and mitigating common vulnerabilities and threats. Some of the key controls covered in the profile include:
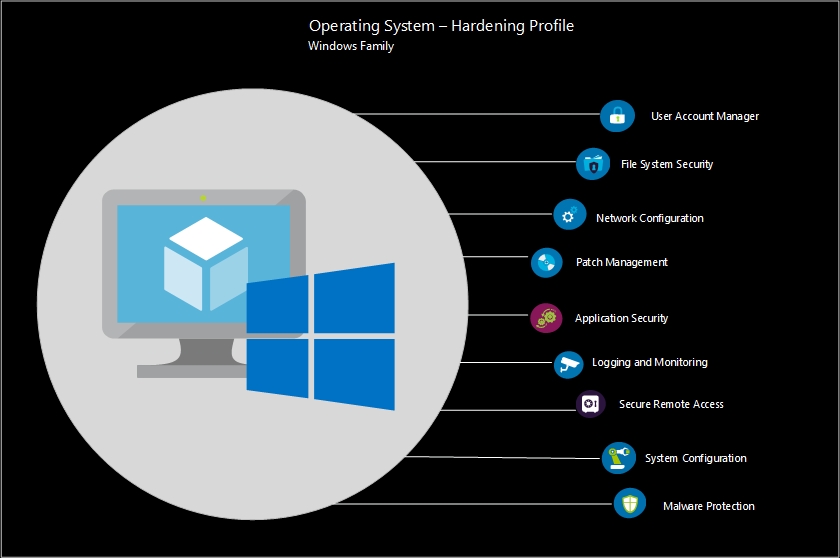
- User Account Management: recommendations for strong password policies, enforcing password complexity, implementing account lockout policies, and managing user privileges.
- File System Security: recommendations for setting appropriate file and folder permissions, securing system directories and files, and implementing access controls to prevent unauthorized access.
- Network Configuration: instructions for securing network settings, including configuring network protocols, securing wireless networks, and implementing secure network communication.
- Patch Management: guidelines for regularly applying security patches and updates to the Windows operating system and installed software applications to address known vulnerabilities.
- Application Security: guidelines for securing applications and preventing common attack vectors, such as configuring application whitelisting, disabling macros in Office documents, and securing web browsers.
- Logging and Monitoring: instructions for enabling and configuring Windows Event Logging, setting up log retention, and monitoring logs for detecting and responding to security incidents.
- Secure Remote Access: recommendations for securing remote access to Windows systems, including the use of secure protocols (e.g., Remote Desktop Protocol), disabling unnecessary remote services, and implementing two-factor authentication.
- System Configuration: guidelines for securing system settings, including disabling unnecessary services and protocols, enabling Windows Firewall, configuring audit policies, and restricting access to critical system resources.
- Malware Protection: recommendations for implementing antivirus and anti-malware solutions, keeping virus definitions up to date, and configuring real-time scanning.
These are some examples of security controls covered in the CIS Hardening Profile for Windows. The profile provides detailed guidance on additional controls, configurations, and best practices to help organizations strengthen the security of their Windows-based systems.
Golden Images
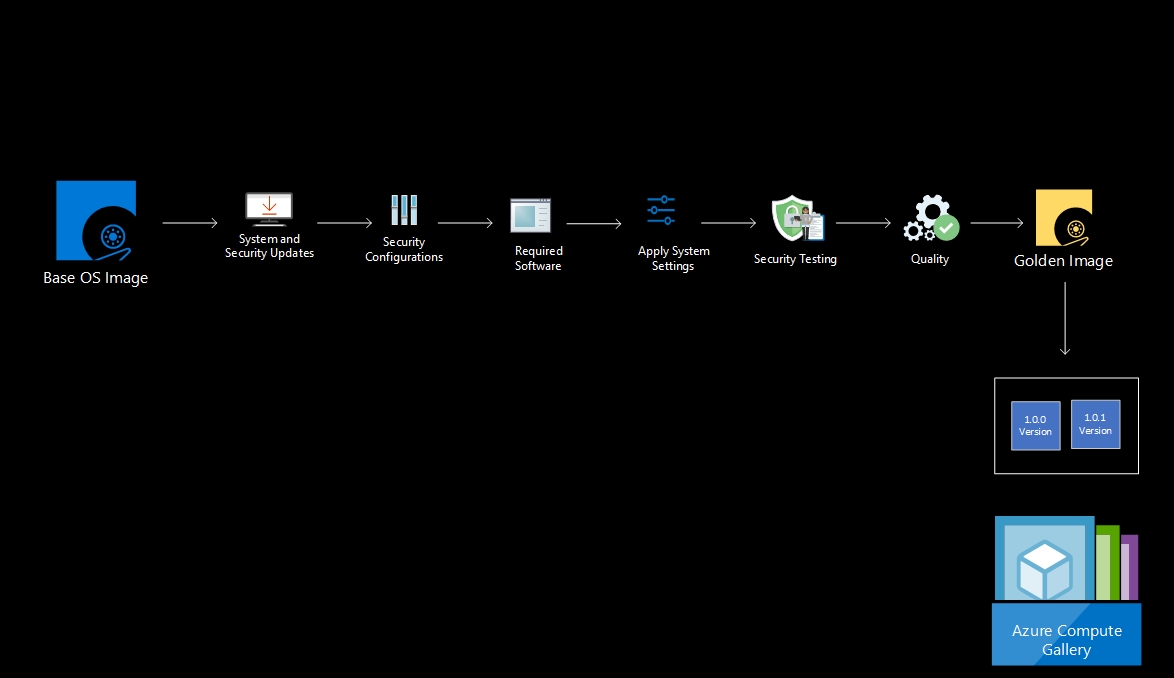
A golden image is a pre-configured and optimized system snapshot that server as a blueprint for creating multiple instances or virtual machines with consistent settings and configurations. It includes the necessary software, security measures, and customizations to ensure streamlined and reliable deployments, saving time and effort in system setup and configuration.
Creating golden images, also known as golden or hardened templates, is a common approach to streamline the deployment of standardized and secure system configurations. Here’s an approach to creating golden images:
- Identify the Purpose: determine the specific purpose or role of the golden image, such as a web server, database server, or virtual desktop. This helps define the necessary software, configurations, and security requirements.
- Start with a Base Image: begin with a clean and up-to-date base image of the operating system or software platform. This can be an Azure Marketplace Image from Microsoft or a CIS Hardening Image.The Azure CIS (Center for Internet Security) Marketplace offer is a collection of pre-configured virtual machine (VM) images available in the Azure Marketplace. These images are built according to the guidelines and best practices outlined in the CIS Azure Foundations Benchmark, which provides security recommendations for Azure deployments.
- Apply Security Updates: install the latest security patches and updates to ensure the base image is secure and up to date. This step helps address known vulnerabilities.
- Harden the Image: follow security best practices and industry guidelines, such as CIS Benchmarks, to harden the image. Configure security settings, disable unnecessary services, and enforce secure configurations to reduce attack surfaces.If you have selected a CIS base image from the Azure Marketplace, it is important to note that these images are already pre-hardened. However, I would advise you to verify that the configurations align with your specific business requirements. It is essential to review and customize the settings as needed to ensure they meet your organization’s unique security and operational needs.
- Install Required Software: add the necessary software components and dependencies for the intended purpose of the golden image. This may include applications, frameworks, libraries, or middleware.
- Configure System Settings: instructions for enabling and configuring Windows Event Logging, setting up log retention, and monitoring logs for detecting and responding to security incidents.
- Implement Security Measures: enhance the security of the golden image by enabling security features, such as firewall settings, encryption protocols, logging and monitoring mechanisms, and antivirus or intrusion detection systems.
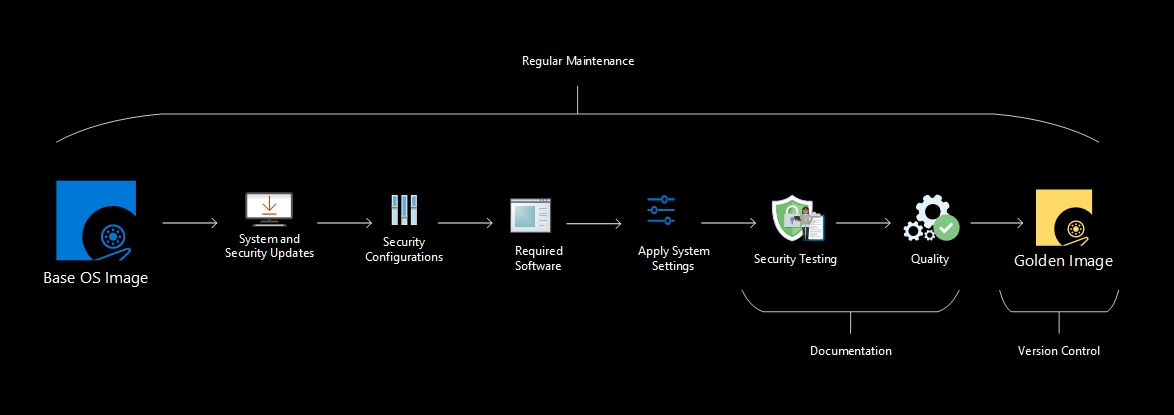
Automating creation Golden Images
Automating the creation of golden images involves implementing a streamlined and repeatable process to generate standardized and secure system snapshots. By leveraging automation tools and frameworks, such as infrastructure-as-code and configuration management, the creation of golden images can be made more efficient. Through automation, the steps for provisioning a base image, applying security configurations, installing required software, and customizing system settings can be scripted and executed programmatically. This allows for consistent and reproducible image creation, reducing manual effort and minimizing the risk of misconfigurations. Furthermore, automation enables organizations to easily update and maintain golden images over time, ensuring that they stay up to date with the latest security patches and configurations.
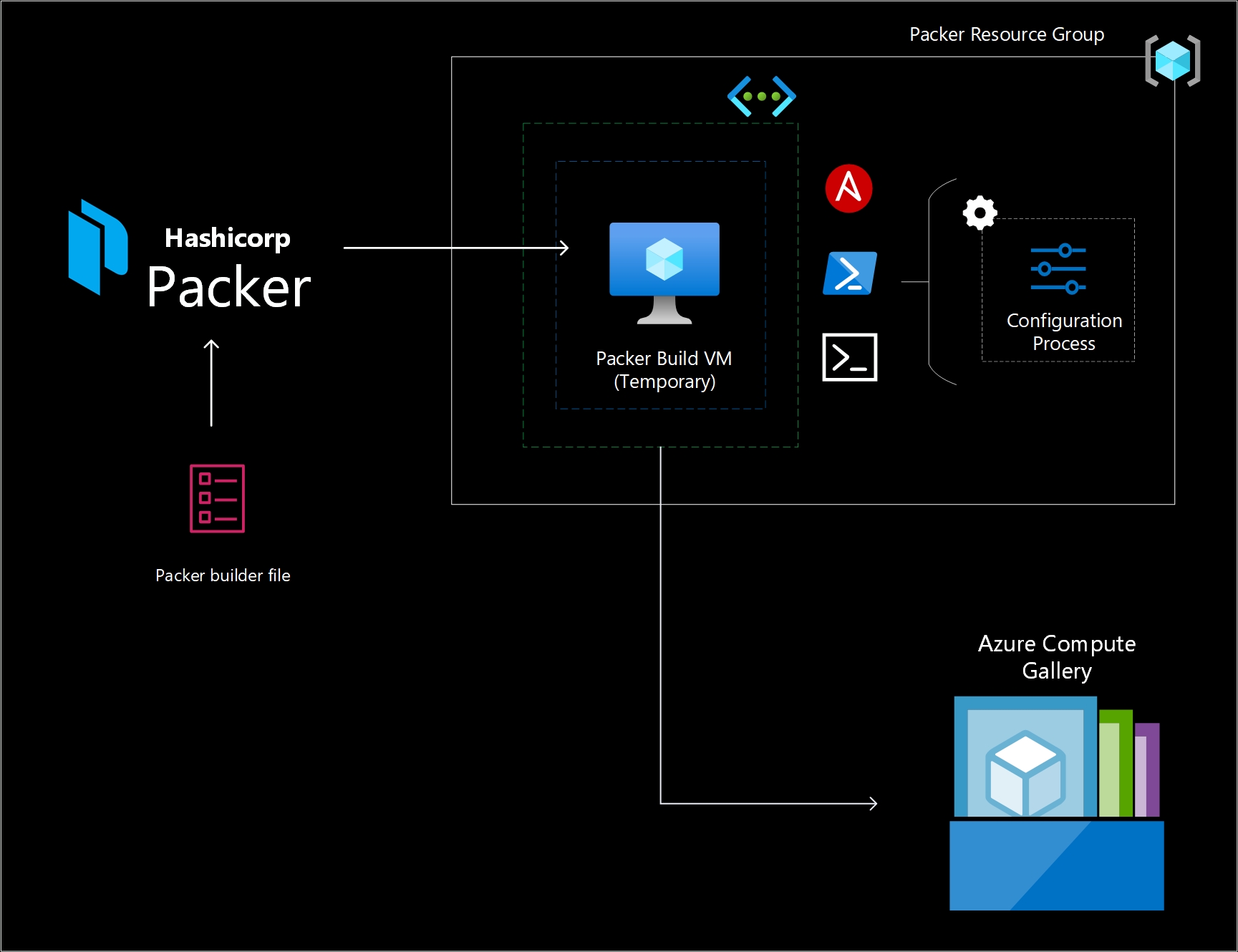
When it comes to creating golden images, I typically rely on Packer as my go-to tool. However, there are other options available in the market, such as Azure Image Builder, or you can even utilize custom scripts to achieve the same result. Packer is a streamlined process that allows you to create custom machine images for cloud platforms like Azure. With Packer, you define a template that specifies the desired configuration and provisions of the image. By running Packer, it communicates with Azure, builds a temporary virtual machine, executes the provisioners, and generates a new machine image. This automated approach ensures consistent and repeatable image creation, enabling efficient deployment and management of Azure resources.
Storing and sharing Golden Images
The Azure Compute Gallery simplifies the organization and management of your Azure resources, including images and applications. It offers the following benefits and functionalities:
- Global replication, the Azure Compute Gallery service is not globally available as a single resource. To ensure effective disaster recovery preparedness, it is recommended to set up a minimum of two galleries in different regions. This approach helps mitigate the risk of a single point of failure and provides redundancy across regions, allowing for failover and continuity in the event of a disaster.
- Versioning and grouping of resources for easier management.
- Highly available resources with Zone Redundant Storage (ZRS) accounts in regions that support Availability Zones. ZRS offers better resilience against zonal failures.
- Sharing to the community, across subscriptions, and between Active Directory (AD) tenants.
- Scaling your deployments with resource replicas in each region.
Hardening Azure Resources
Hardening Azure resources involves implementing security measures and configurations to strengthen the security posture of your Azure infrastructure. The Microsoft Cloud Security Benchmark (MCSB) offers actionable best practices and recommendations to enhance the security of workloads, data, and services within Azure and multi-cloud environments. This benchmark prioritizes cloud-centric control areas and incorporates insights from comprehensive Microsoft and industry security guidance. Key components of the benchmark include:
- Security Controls: the benchmark covers a wide range of security controls, including access management, network security, data protection, identity and authentication, monitoring and logging, secure development, and more.
- Compliance Standards: the Microsoft Cloud Security Benchmark aligns with various industry-recognized security standards and frameworks, such as the Center for Internet Security (CIS) controls, National Institute of Standards and Technology (NIST) guidelines, and Microsoft’s internal security requirements.
- Recommendations and Prescriptive Guidance: the benchmark provides prescriptive guidance and recommendations for implementing security controls in Azure. It offers detailed explanations, configuration steps, and best practices to help organizations effectively secure their Azure resources.
- Azure Policy and Microsoft Cloud Defender Integration: the Microsoft Cloud Security Benchmark can be implemented through Azure Policy, allowing organizations to enforce security controls and configurations across their Azure environment. It also integrates with Microsoft Cloud Defender to provide a consolidated view of security posture and compliance.
- Continuous Updates: Microsoft regularly updates the this framework to address emerging threats, incorporate new security features, and reflect changes in Azure services. It is important to stay up to date with the latest version to ensure the effectiveness of security measures.
- Customization and Tailoring: organizations can customize and tailor the benchmark to meet their specific security requirements and compliance needs. It provides a flexible framework that can be adjusted based on the organization’s risk profile and industry regulations.
By leveraging the Microsoft Cloud Security Benchmark, organizations can assess their Azure environment against industry-recognized security controls, implement recommended security configurations, and enhance the overall security posture of their Azure resources. It serves as a valuable resource for organizations looking to establish and maintain a strong security foundation in their Azure deployments.
Next post
In the process of hardening, the goal is to strengthen system security and reduce the possibilities of vulnerability exploitation. It is crucial to disable or remove any unnecessary items or configurations that could create new security loopholes.
By performing hardening, you eliminate potential weak points and reduce the attack surface. This involves disabling unused services and resources, removing unnecessary users or accounts, applying recommended security configurations, regularly updating software, and implementing stringent control measures.
In the next post, I will delve into the significance of monitoring and auditing as essential elements of a comprehensive security strategy. These practices play a vital role in providing visibility into the activities and events taking place within an environment.
Leave a Reply